Introduction
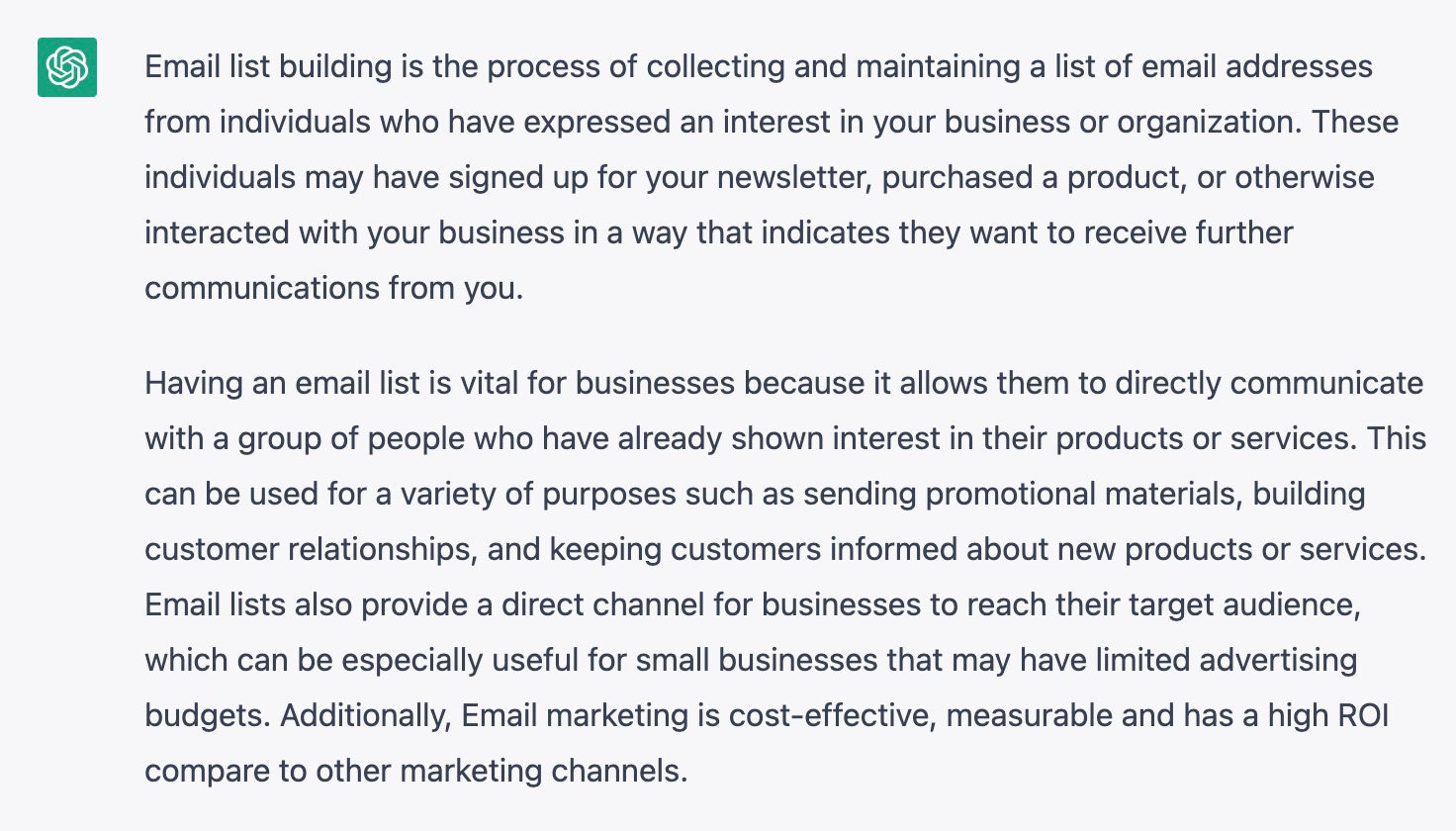
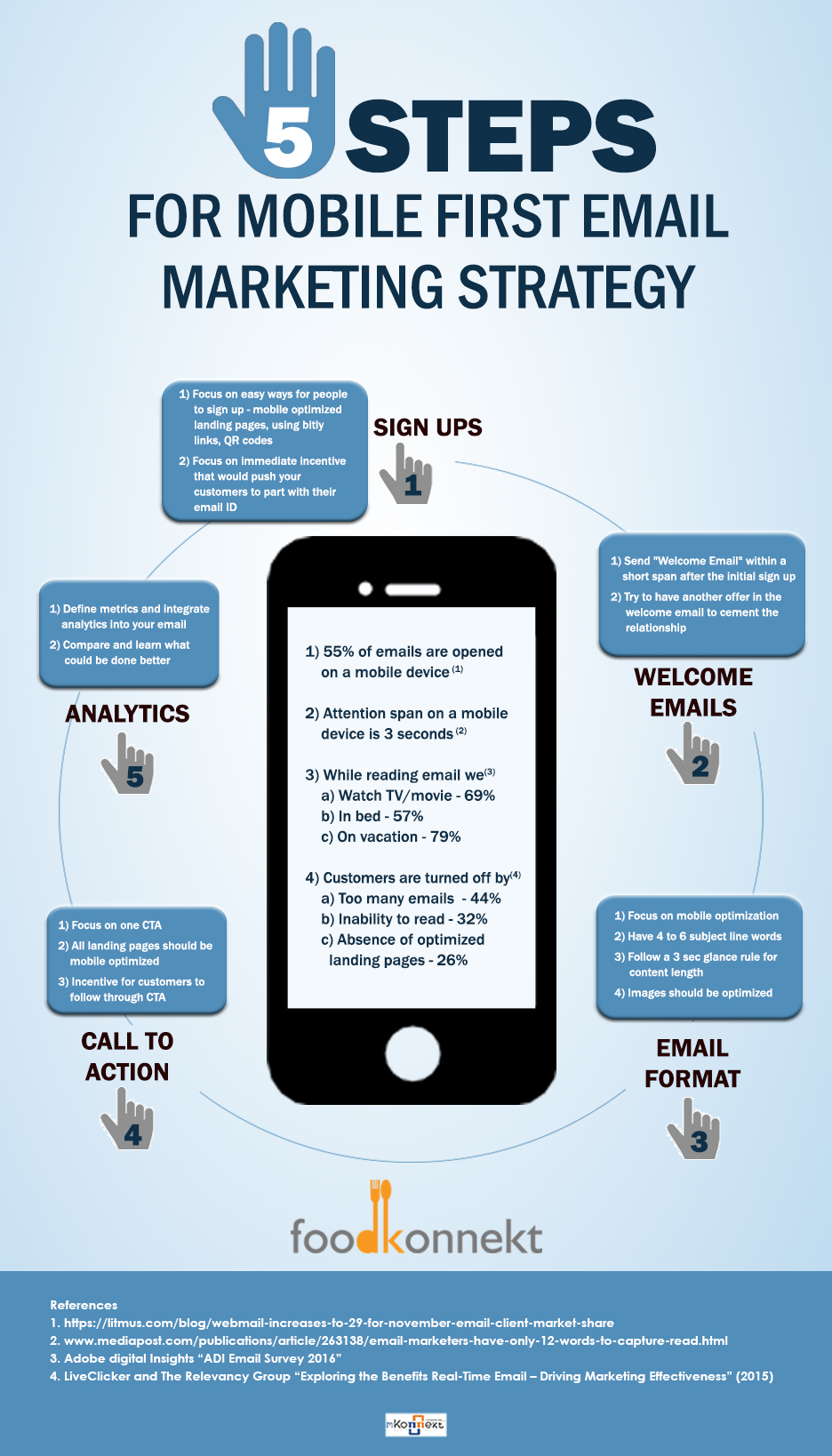
SMS marketing offers higher open rates and immediacy, while email marketing provides more detailed content and customization options. SMS and email marketing each have unique advantages.
SMS marketing boasts an impressive open rate, often as high as 98%, making it ideal for urgent messages and promotions. It’s a direct line to your audience, ensuring they receive your message almost instantly. Email marketing, on the other hand, allows for more comprehensive communication.
It’s perfect for newsletters, detailed product information, and segmented campaigns. Emails can be customized with rich media, links, and longer content. Both channels can complement each other in a well-rounded marketing strategy, delivering timely and relevant information to your audience in the most effective manner.
Introduction To Sms And Email Marketing
SMS and Email Marketing are popular tools. They help businesses reach customers quickly. Each has its unique strengths. Understanding both can improve your marketing strategy.
The Rise Of Digital Marketing
Digital marketing has grown fast. It offers many ways to connect with customers. SMS and email are two of these ways.
- SMS is short and direct.
- Email allows for longer messages.
- Both are cost-effective.
Inbox Attention Wars
Getting attention in an inbox is hard. Both SMS and email face this challenge.
Let’s compare:
| SMS | |
|---|---|
| Higher open rate | More space for content |
| Limited characters | Can include images and links |
| Immediate delivery | Can be scheduled |
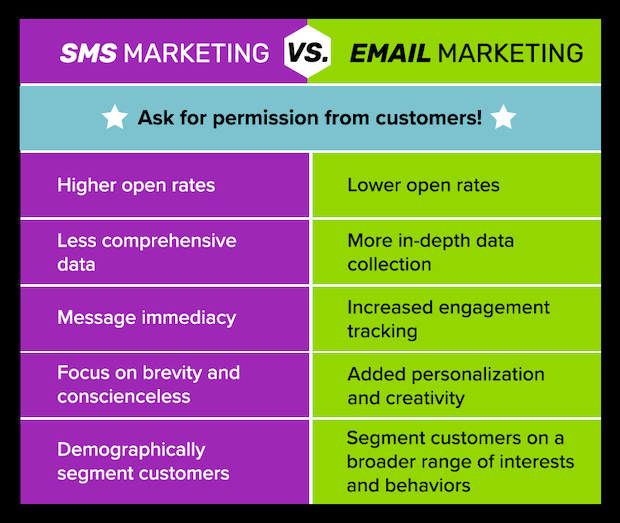
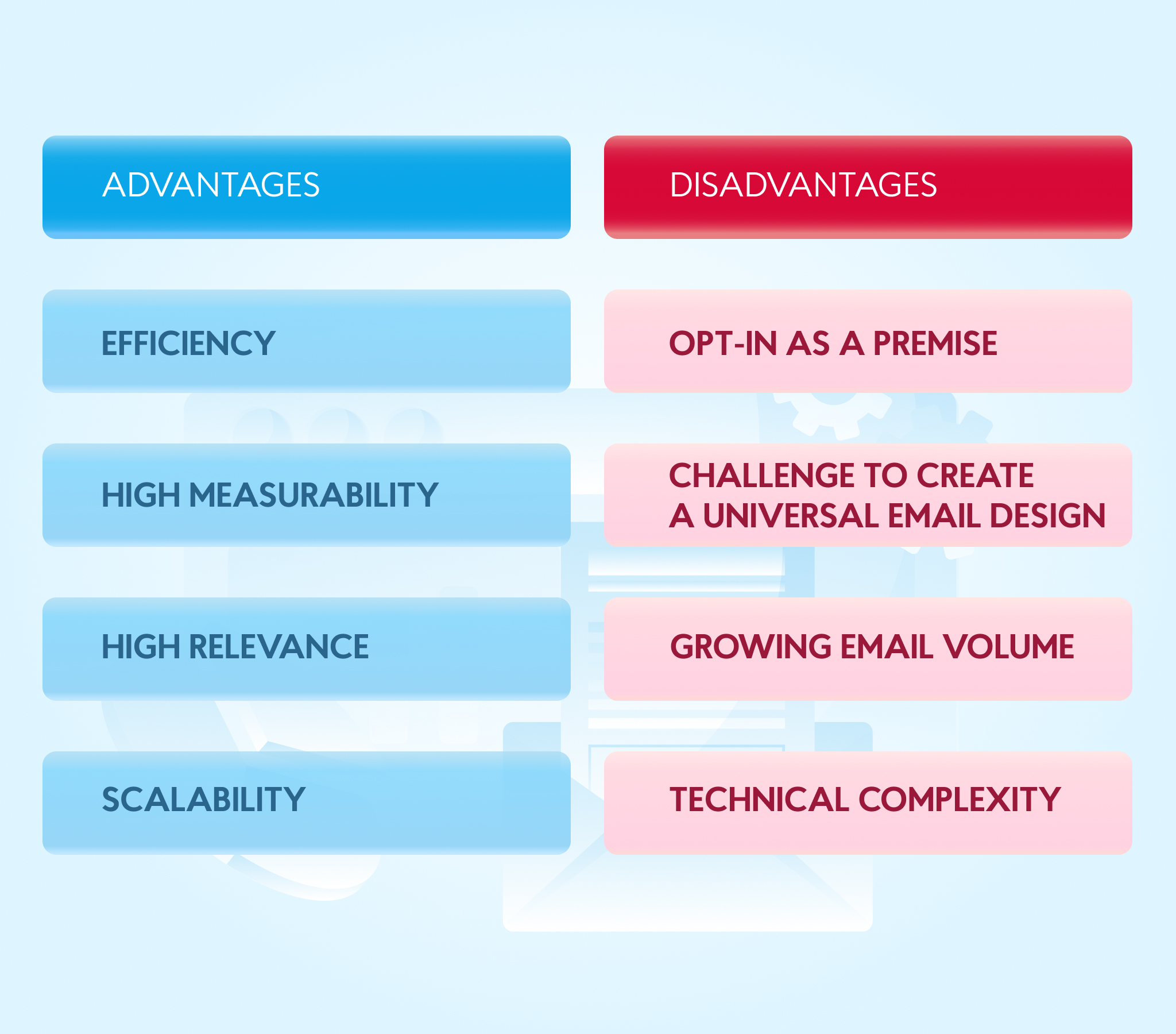
Core Advantages Of Sms Marketing
SMS marketing offers unique benefits compared to email marketing. These advantages make it a strong choice for businesses. Let’s explore the core advantages of SMS marketing.
Immediate Delivery And Open Rates
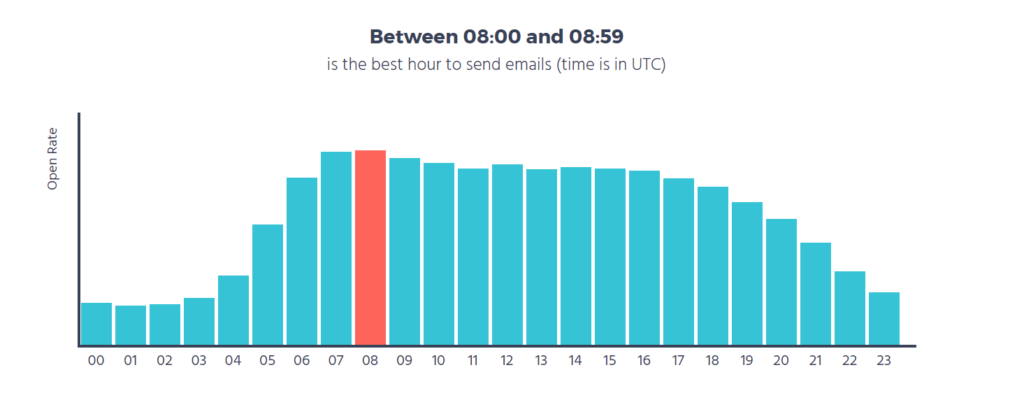
SMS messages reach users instantly. Most people read texts within minutes. This quick delivery ensures your message gets seen fast.
Open rates for SMS are very high. Around 98% of text messages get opened. This is much higher than email open rates. Your message is more likely to be read.
Personal Touch And High Engagement
SMS allows for a personal touch. You can address users by name. This makes the message feel more direct and friendly.
Users engage more with text messages. They are more likely to respond or take action. SMS marketing creates a strong connection with your audience.
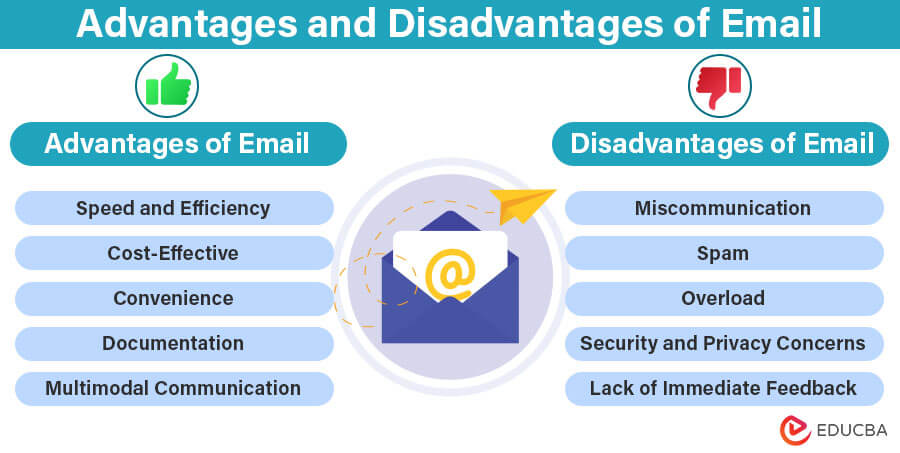
Benefits Of Email Marketing
Email marketing is a powerful tool for businesses. It offers many benefits that can help you reach your goals. Here, we explore some key advantages of using email marketing.
Rich Content Capabilities
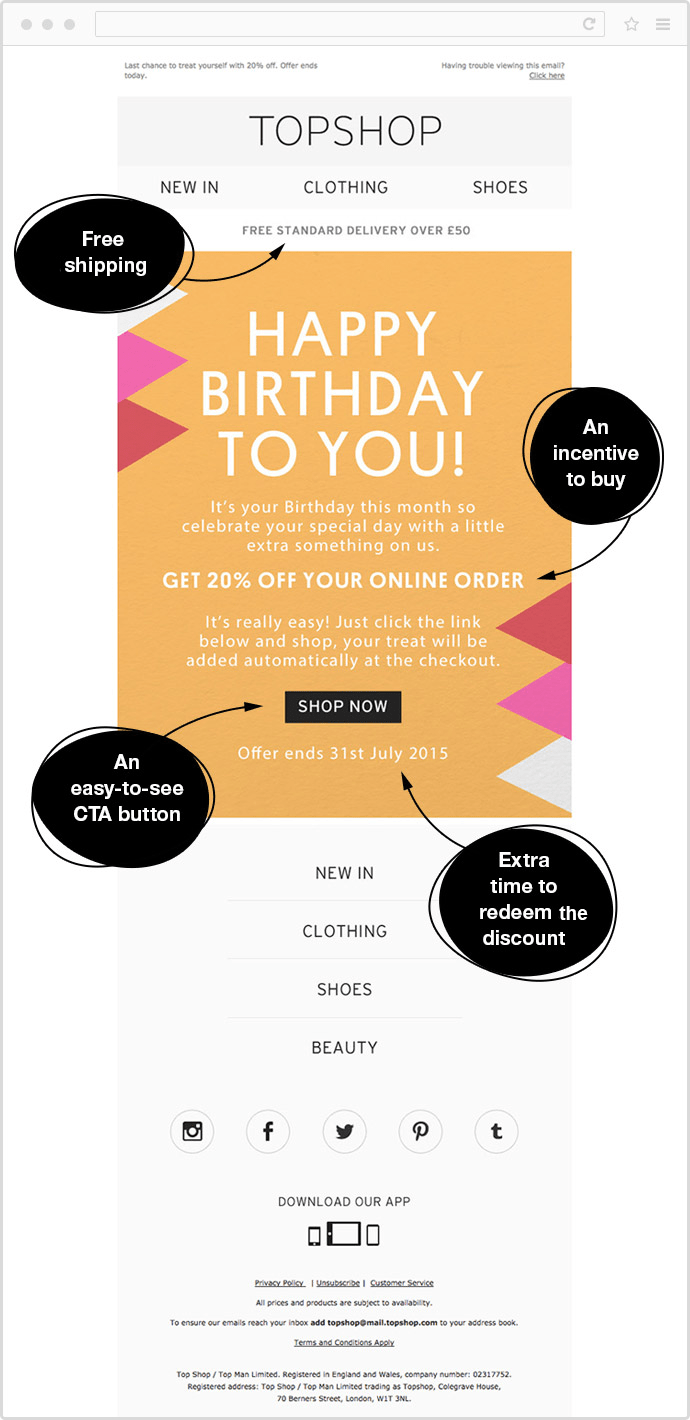
Emails allow for rich content. You can use images, videos, and links. This makes your message engaging. You can also use different fonts and colors. This helps to catch the reader’s eye.
Emails can be tailored to suit your brand. You can include your logo and brand colors. This helps to build brand recognition. Rich content makes your emails more appealing.
Detailed Analytics And Segmentation
Emails offer detailed analytics. You can track open rates, click-through rates, and conversions. This helps you understand how your emails perform.
Segmentation allows you to target specific groups. You can send different messages to different audiences. This makes your emails more relevant. Targeted emails can improve engagement and conversions.
| Metric | What It Measures |
|---|---|
| Open Rate | How many people open your email |
| Click-Through Rate | How many people click on links |
| Conversion Rate | How many people take desired actions |
Using these metrics, you can refine your strategy. This makes your campaigns more effective.
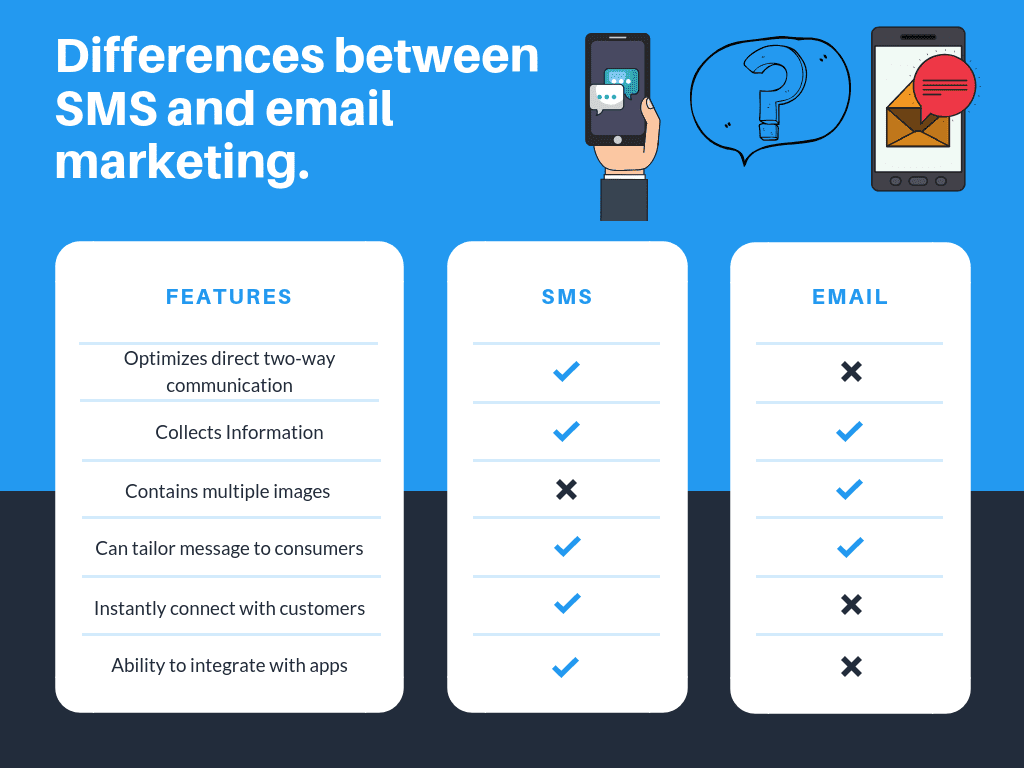
Comparative Analysis: Reach And Accessibility
Comparing SMS and email marketing involves looking at their reach and accessibility. Both methods have distinct advantages. Each has its own unique limitations and benefits. This section explores these aspects in detail.
Global Reach And Internet Requirement
Email marketing relies heavily on internet access. A stable internet connection is necessary to send and receive emails. This can be a limitation in areas with poor connectivity.
SMS marketing, on the other hand, does not require internet access. Mobile networks are more widespread than internet services. This makes SMS accessible in remote areas where internet may be unavailable.
Here’s a comparative table illustrating the internet requirements for both methods:
| Marketing Method | Internet Requirement |
|---|---|
| Email Marketing | High |
| SMS Marketing | Low |
Mobile Penetration And Instant Access
Mobile phones are widely used globally. SMS marketing leverages this high mobile penetration. People often have their mobile phones with them at all times.
This results in instant access to messages. SMS marketing ensures your message reaches the recipient almost immediately.
Email marketing does not offer this level of instant access. Emails may sit in inboxes for hours or even days before being read. Notifications for emails are often turned off, delaying their reading.
Consider these points:
- SMS messages are read within minutes of delivery.
- Emails can be read much later.
- Mobile phones are more accessible than computers.
Audience Engagement
Engagement rates differ between SMS and email marketing. SMS marketing generally sees higher engagement rates.
Emails can get lost in crowded inboxes. SMS messages are more likely to be opened and read.
Here’s a quick comparison:
- SMS: Higher open rates
- Email: Lower open rates
- SMS: More immediate engagement
- Email: Delayed engagement
Understanding these differences helps in choosing the right marketing strategy. Both SMS and email have their strengths. The choice depends on your specific needs and audience.
Cost Efficiency And Roi
Cost efficiency and ROI are key factors in marketing. Both SMS and email marketing offer unique benefits. Let’s dive into their cost efficiency and ROI.
Budget-friendly Marketing Solutions
SMS marketing is often seen as cost-effective. It involves a low cost per message. Bulk SMS services further reduce costs.
Email marketing can be cheaper. Sending emails costs less, especially with bulk email providers. Both methods require low investment but yield high engagement.
Return On Investment Metrics
ROI is crucial for marketing. SMS marketing often shows higher open rates. Many people read SMS within minutes. This quick engagement boosts ROI.
Email marketing has a different ROI metric. It is measured over longer periods. Email campaigns can nurture leads and convert them.
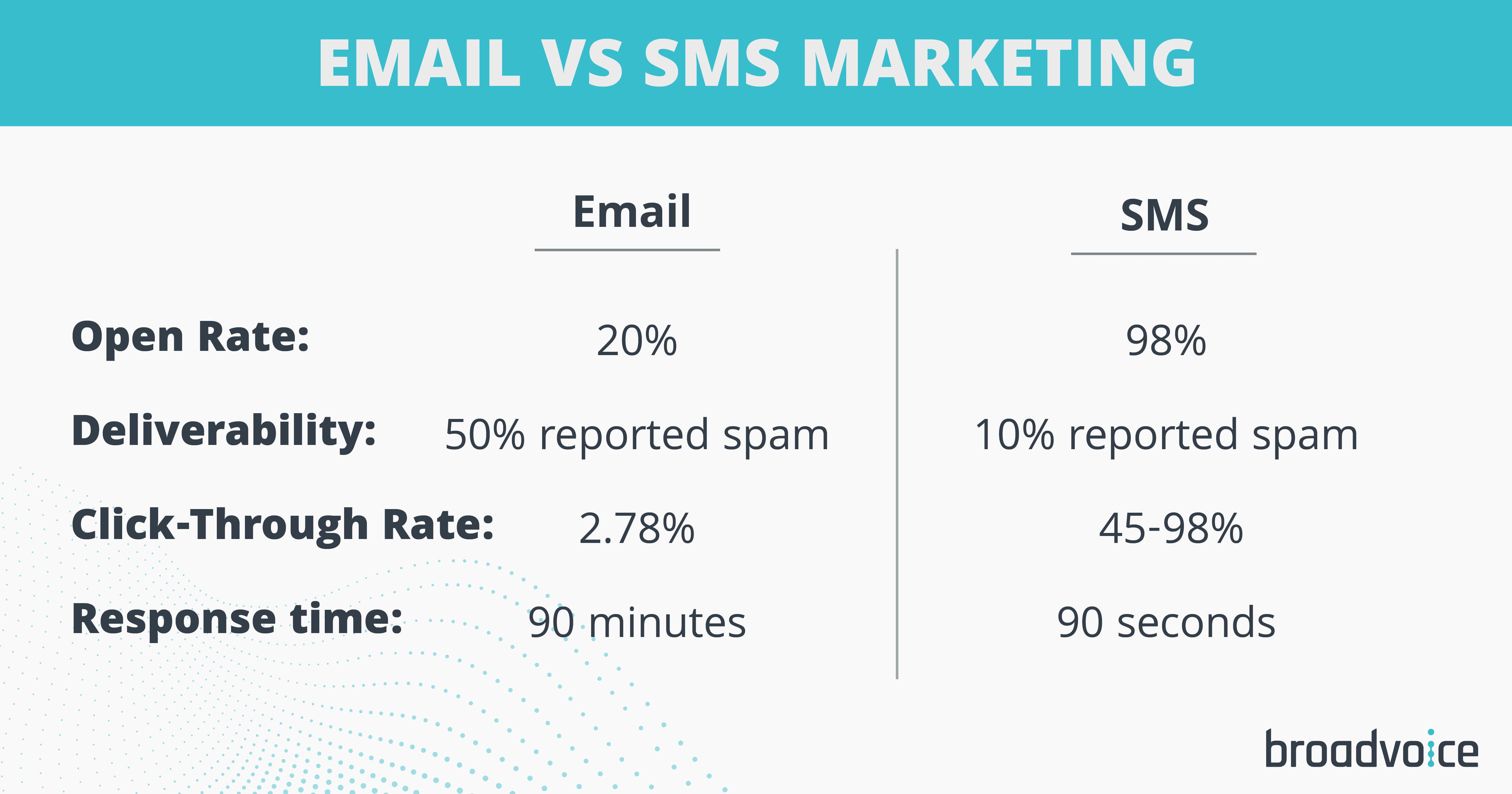
Below is a table comparing the ROI of SMS and email marketing:
| Metric | SMS Marketing | Email Marketing |
|---|---|---|
| Open Rate | 98% | 20% |
| Click-Through Rate | 36% | 3.2% |
| Response Time | Within 3 minutes | Within 24 hours |
| Cost Per Message | $0.01 – $0.05 | $0.001 – $0.02 |
Both SMS and email marketing offer great ROI. SMS is faster but can be costlier per message. Email is slower but cheaper per message.
User Preferences And Behavior
Understanding user preferences and behavior is key to choosing between SMS and email marketing. Both channels offer unique advantages. The right choice depends on how your audience prefers to communicate. Below, we delve into consumer communication preferences and opt-in and privacy considerations.
Consumer Communication Preferences
Consumers have different preferences for communication. Some prefer the immediacy of SMS. Others appreciate the detailed content that emails can provide. Understanding these preferences can help tailor your marketing strategy.
| Communication Channel | Preferred By |
|---|---|
| SMS | People who need quick updates |
| People who prefer detailed information |
SMS messages are often read within minutes. They are ideal for urgent updates. Emails, on the other hand, allow for more in-depth content. They are better for detailed promotions or newsletters.
Opt-in And Privacy Considerations
Opt-in and privacy are crucial in marketing. Users must give consent before receiving messages. This applies to both SMS and email marketing.
- Ensure users can easily opt-in.
- Provide clear information on what they will receive.
- Respect user privacy and data protection laws.
For SMS, users often need to text a keyword to a short code. For emails, users usually sign up through a form on your website. Both methods should include a clear privacy policy.
Respecting user privacy builds trust. It also ensures compliance with laws like GDPR and CAN-SPAM.
Integrating Sms And Email For A Robust Strategy
Combining SMS and email marketing creates a powerful strategy. Each channel has unique strengths. Together, they enhance engagement, reach, and conversion rates. This approach ensures messages reach your audience effectively.
Multi-channel Marketing Approaches
Using both SMS and email marketing offers a multi-channel approach. Each channel complements the other. SMS is quick and direct, while email provides detailed information.
| SMS | |
|---|---|
| Immediate reach | Detailed content |
| High open rates | Customizable design |
| Short, concise messages | Long-form content |
Combining these channels enhances your marketing reach. Use SMS for urgent updates and reminders. Use email for newsletters, promotions, and detailed information.
Creating A Cohesive User Experience
Creating a cohesive user experience is crucial. Ensure your messages are consistent across channels. Use similar branding, tone, and style. This builds trust and recognition.
- Use consistent branding across SMS and email.
- Maintain a similar tone and style.
- Coordinate message timing to avoid overload.
- Personalize messages for better engagement.
Consistency in messaging enhances user experience. It makes your brand more reliable and trustworthy. This leads to higher engagement and customer satisfaction.
Case Studies: Successful Campaigns
Businesses need effective marketing strategies. SMS and Email are two popular options. Let’s explore successful campaigns for both methods. Learn which could work best for you.
Innovative Sms Marketing Campaigns
SMS marketing can reach customers instantly. Here are some successful examples:
- Brand A: Increased sales by 30% with flash sales alerts.
- Brand B: Boosted engagement by 40% using personalized messages.
- Brand C: Achieved a 95% open rate with time-sensitive offers.
| Brand | Strategy | Result |
|---|---|---|
| Brand A | Flash sales alerts | 30% sales increase |
| Brand B | Personalized messages | 40% more engagement |
| Brand C | Time-sensitive offers | 95% open rate |
Email Marketing Wins And Insights
Email marketing allows for detailed messages. Here are some winning examples:
- Company X: Achieved a 50% open rate with targeted newsletters.
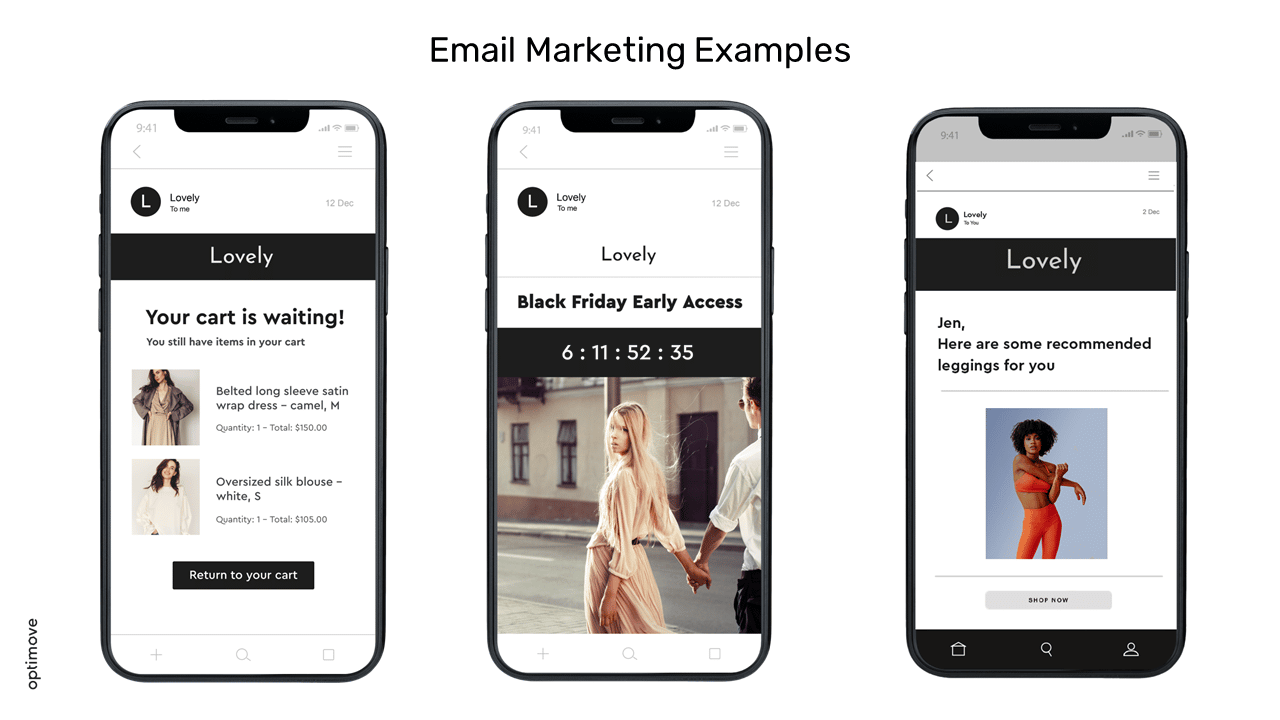
- Company Y: Increased conversions by 20% with abandoned cart emails.
- Company Z: Boosted customer loyalty with personalized offers.
| Company | Strategy | Result |
|---|---|---|
| Company X | Targeted newsletters | 50% open rate |
| Company Y | Abandoned cart emails | 20% more conversions |
| Company Z | Personalized offers | Improved customer loyalty |
The Future Of Inbox Marketing
The world of inbox marketing is changing fast. SMS and email marketing both have unique strengths. They help businesses reach their audience effectively. But what does the future hold for these two channels? Let’s explore the emerging technologies and trends, and predictions for their evolution.
Emerging Technologies And Trends
New technologies are shaping how we use SMS and email marketing. Artificial Intelligence (AI) and machine learning are big players. They help marketers understand customer behavior better. This means more personalized messages.
Chatbots are also becoming popular. They engage with customers in real-time. This boosts customer satisfaction. Another trend is the use of rich media. Images, videos, and GIFs make emails and SMS more engaging. People are more likely to respond to them.
Here are some emerging trends in inbox marketing:
- AI and machine learning for personalized messages
- Chatbots for real-time engagement
- Rich media in emails and SMS
- Interactive emails with polls and surveys
- Omni-channel marketing strategies
Predictions For Sms And Email Evolution
Both SMS and email marketing will continue to evolve. SMS will become more interactive. Features like clickable links and QR codes will be common. This will make it easier for users to engage with brands.
Email marketing will see more automation. Drip campaigns and triggered emails will be the norm. This means emails will be sent based on user actions. For example, if someone visits a product page but doesn’t buy, they get a reminder email.
Here is a table summarizing future trends for SMS and email marketing:
| Feature | SMS Marketing | Email Marketing |
|---|---|---|
| Interactivity | Clickable links, QR codes | Polls, surveys |
| Automation | Automated responses | Drip campaigns, triggered emails |
| Personalization | Location-based offers | Behavior-based offers |
| Rich Media | Images, videos | GIFs, interactive elements |
In summary, the future of inbox marketing looks bright. Both SMS and email will continue to grow. They will become more interactive and personalized. By leveraging new technologies, marketers can create more effective campaigns.
Final Thoughts
Deciding between SMS and email marketing can be tough. Each channel offers unique benefits. Understanding your audience can help you choose wisely. Here are some final thoughts to consider.
Choosing The Right Channel For Your Audience
Know your audience well. Different groups prefer different channels. Younger people may like SMS. Older people may prefer email. Use analytics to see which channel works best. Try sending surveys to ask your audience directly. This helps tailor your approach.
Best Practices For Engaging Customers
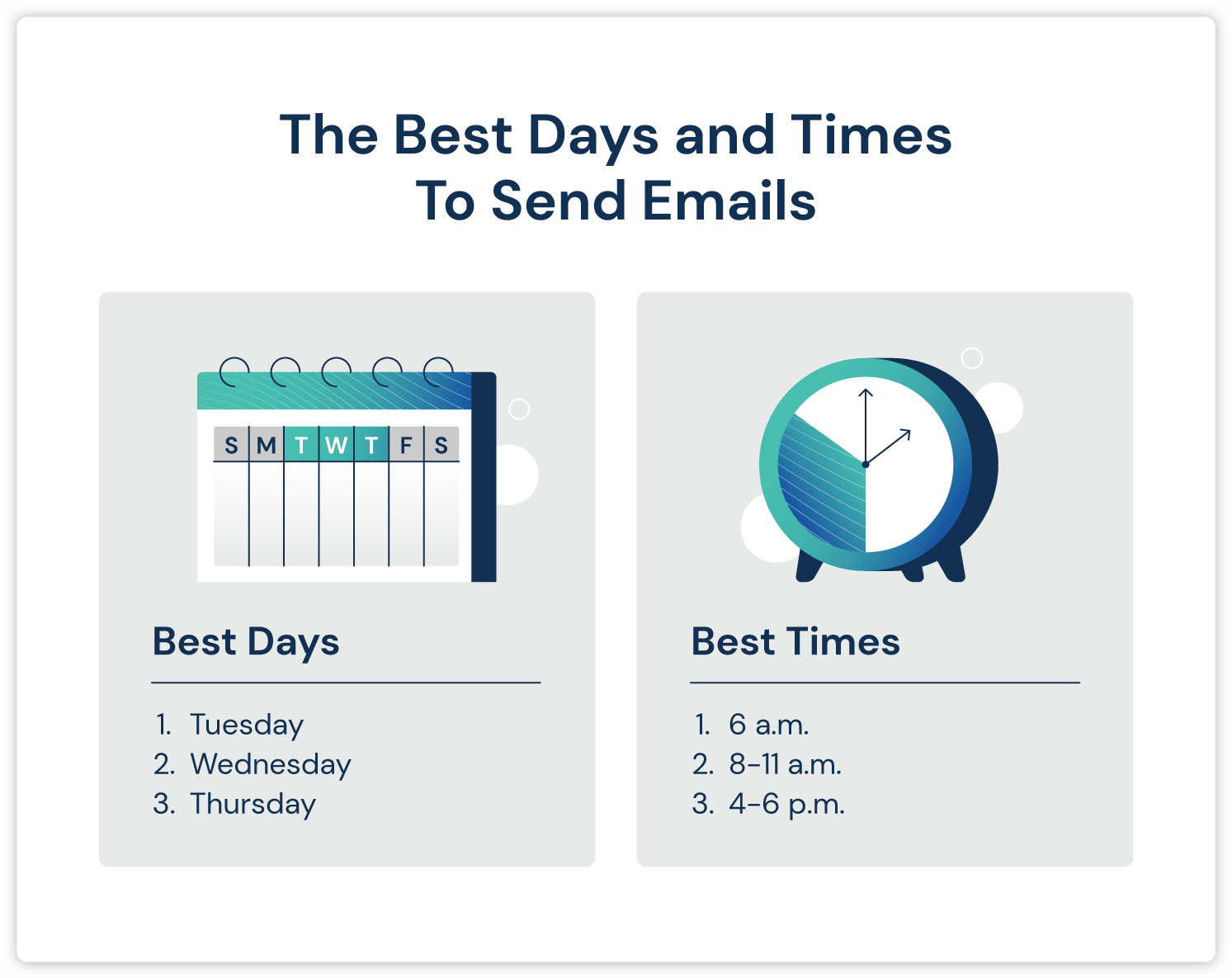
Keep your messages short and clear. Long messages can bore readers. Use a friendly tone. Personalize your messages with names or past actions. Offer value in every message. This could be a discount or helpful info. Test different times to send messages. See what gets the best response.
| Channel | Benefits | Drawbacks |
|---|---|---|
| SMS | High open rates, Instant delivery | Limited characters, Can be intrusive |
| Detailed messages, Easy to track | Lower open rates, Can go to spam |
- Use A/B testing to find the best content.
- Always get permission before sending messages.
- Make it easy to opt-out.
- Analyze your audience data regularly.
- Adjust your strategy based on feedback.
- Stay updated with industry trends.
Following these tips can help you succeed. Choose the right channel. Engage your customers effectively.
Frequently Asked Questions
Which Is Better, Sms Marketing Or Email Marketing?
Both SMS and email marketing have benefits. SMS offers higher open rates and immediacy. Email provides more content space and detailed analytics. Choose based on your audience and goals.
Is Sms Or Email More Effective?
SMS is often more effective for immediate communication. Email is better for detailed information and marketing. Both have unique strengths.
Is Sms Marketing Still Effective?
Yes, SMS marketing remains highly effective. It boasts high open rates, instant delivery, and strong engagement. Businesses benefit from its direct approach, reaching customers quickly.
What Is The Response Rate Of Sms Vs Email?
SMS response rates are around 45%, while email response rates average only 6%. SMS is more immediate and engaging.
Conclusion
Choosing between SMS and email marketing depends on your goals and audience. SMS offers quick engagement, while email provides detailed content. Both have unique advantages. Evaluate your strategy and utilize both to maximize reach. Effective marketing combines the strengths of each method, ensuring your message resonates with your target audience.